....and all those jargon. What is it? Why do we need it?
There are many security products and applications. #SIEM, #Antivirus, #DLP, #Firewalls, #VPN, #IPS, #IDS, #IDM, #AAA…and the list goes on. Why are organisations having a problem with it still?
Are these some questions you have asked yourself? In this article I try to throw some light on them. I might skip a few points or scenarios to keep it short, I will however ensure the important topics are covered.
Have you ever thought that possibly even our grandparents knew the concept of security? Imagine a proverbial diamond ring given to your grandma by your grandpa to be worn for special occasions. How would she store and secure it? I would like to imagine that she would store it in her bedroom, in a possible safe or a metal storage unit which usually has a miniature locker. Then she would ensure it is locked. Then lock the storage unit when not in use. When she leaves home she would possibly lock the bedroom and the main door. Possibly in those days a dog would roam the garden around the house. Easy isn't it?Remember this analogy,
Oh yes for those of who would would say, “Hey buddy, I wouldn’t beat myself blue on this, I will just pop it into my bank locker and be done with security”. While it is a simple approach to security, We have all heard of Bank heists where lockers have been violated. Interestingly most Banks cannot compensate for what you have lost in lockers as they are not privy to what you are storing in them. Interesting isn’t it? We will come to cloud related storage scenarios later in the article.
A brief History of time in the IT infrastructure arena. Migrating Data zones.
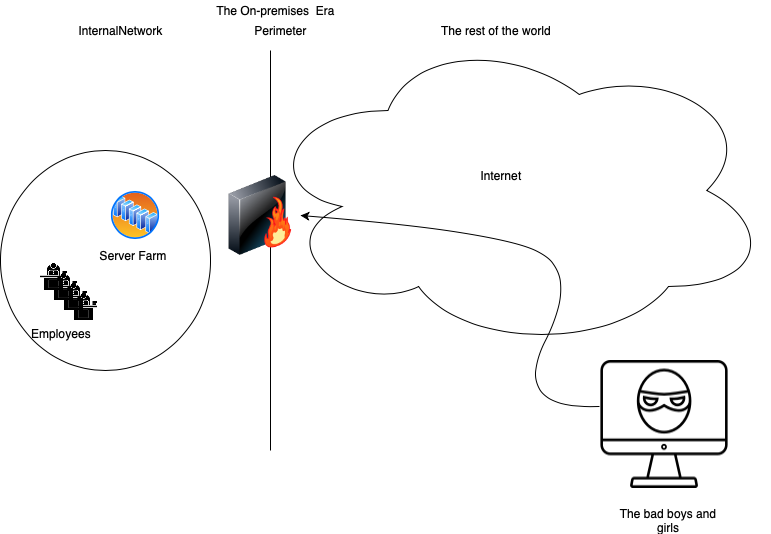
Once upon a time there was only on-premises Infra:
1#On-Premises Era: Data was centralised on premises, data was contained inside corporate networks.
Ever since the popularity of X86 and Intel Personal computers, organisations and people started to use and store data in their personal computers or servers located in their premises. This scenario was easy to understand. You defined a perimeter, brought in perimeter security, locked-down your servers, secured the physical location and you were mostly done. You had an administrator who handled issues.
If you equate #criticaldata to say the Royalty during the medieval ages, The King and Queens as may be, along with the extended royal family stayed in their kingdom in their designated palaces protected by their military forces.
Then came Co-location
Note: all diagrams are purely illustrations to drive a point home and might not be architecturally accurate.
#Co-location Era: With public accessible services being offered by organisations and distributed work environments, On-Premises became a bottleneck and a large amount of data moved to co-located servers in reliable datacenters. This created a uniq scenario where the perimeter was diluted. You no longer had a single front to defend, you had to secure multiple fronts. In came VPNs, Secure access such as SSH, SFTP and other technologies to maintain confidentiality to and from your office location to on-premises servers.
Technologies:: VPNs, SSH, SFTP...
This created an interesting scenario to malicious individuals (notice I am not using the word Hackers, there are too many arguments on the term) because, other than your protection cover of encrypted/dedicated communications to your servers located in distant datacenters, in terms of reachability to the remote zone, your reach was as good as an opportunistic malicious individuals reach. I will not argue the plethora of security technologies and terminologies that came up. However, understand that you have taken your coveted data from your strong-hold inside your premises and placed it in the strong hold of another organization who guarantees security.
This is the equivalent of taking the Royal Family of your kingdom and moved him and family lock stock and barrel from the midst of multiple battlements, multiple security forces, and moats with crocodiles and other poisonous reptiles to a palace in the some distant land which promises a comfortable and secure accommodation to your King and family. Interesting?
Then came Cloud..
Cloud Era: With Consolidation, Virtualization and subsequent Cloud technologies coming to the fore, Cloud services providers were able to provide you with systems at a cheaper rate then Co-located servers. These were reliable and certain infrastructure services streamlined. This made it convenient for IT teams to decide and migrate data to the cloud. No capex, no EOL management, No hardware teams or vendors needed for your Computing systems, Higher reliability, expenses written off rather than claim depreciation benefits and the Penetration of Large bandwidth providers made this attractive. It was a dream come true to many organisations and IT teams moved their King and Queens to the cloud, at the cloud providers premises. These locations were better protected, lot more moats, lots of crocs and reptiles. Full menu of services. Why not? In fact they were so good, many other kingdoms moved their Kings and Queens to the same location. When they got bored the many royal pairs would have dinners or dance balls together!! Man that was a happy scenario for any kingdoms with Royalty to please. Besides it is cheap!! Why not move the Royal children who were still back home to the Cloud? Why not their uncles and aunts, what about the Royal Siblings who missed the Title? Send them there, it is cheap, it is convenient and the environment is secure apparently !!
I think we get the drift! In this phase organisations started to move all their critical data to the cloud as it is convenient and cheap. Can you think of another adage? All the eggs in one basket ! This brought in evolution of Internet Criminals where they now grouped together and brought in superior forces to bring down the complex and secure walls. Why? Because the price made it affordable ! Poke a hole in that defence and you have many prices for the taking. In fact this was even better than ransoming the Kings and Queens back to their kingdoms! With Data as a commodity, you could sell them to multiple buyers !!!!! This made it attractive to the bad guys to Engineer ever complex attacks, Spend longer time to break through, Ramp up on talent from different geographical locations. The target is on cloud dear friends they are as close to you as to some one sitting in Timbuktu.
#Billshock, News of data leakages after compromises of cloud instances
Hybrid Cloud, We are today here ..
#HybridCloud or the #VPCs Era: This is apparently the phase most enlightened organizations are today, in mid 2019. The centralised Kings palaces in the distant lands started to provide newer and newer services and the kings and queens started to like it lots !!! The prices started to go up and at the same time there was enough evidence that the big bad boys had built a bag full of Siege machines, big and mean enough to breach the big fat walls of the centralised Palace or Palaces for multiple Royal Families. There was also considerable delay in some communications / decisions as the information had to flow from the respected kingdoms to the Centralised Palace ( #IoT traffic). The situation became troubling to the Kingdoms back home. Bigger and Bigger bills month on month and the risk of losing the Royalty to the bad guys.
So the kingdoms decided to move a section of their royalty back to home ground or other safer locations based on security and pricing.
Using #Dataclassification, Costs, Impact of loss costs and various other parameters organisations decided to position data on multiple Cloud providers and On-premises based on need and utilisation.
#edgecomputing, #VPC
So now we know that you have data that is valuable to yourself and others, it is time to look at how to secure it...
Will talk about it in the next article..
 June 22,2019
June 22,2019
 Dec 09,2020
Dec 09,2020
 March 05,2021
March 05,2021
Copyright 2025 Luminet.
Thank you for contacting us. Our team will get back to you shortly